While working on our automatic configuration extractors, we came across a rather strange-looking Vidar sample.
The decrypted strings included domain names of such organizations as the NATO Strategic Communications Centre of Excellence, Border Guard of Poland, Estonia and Latvia, and Ministry of the Interior of Lithuania.
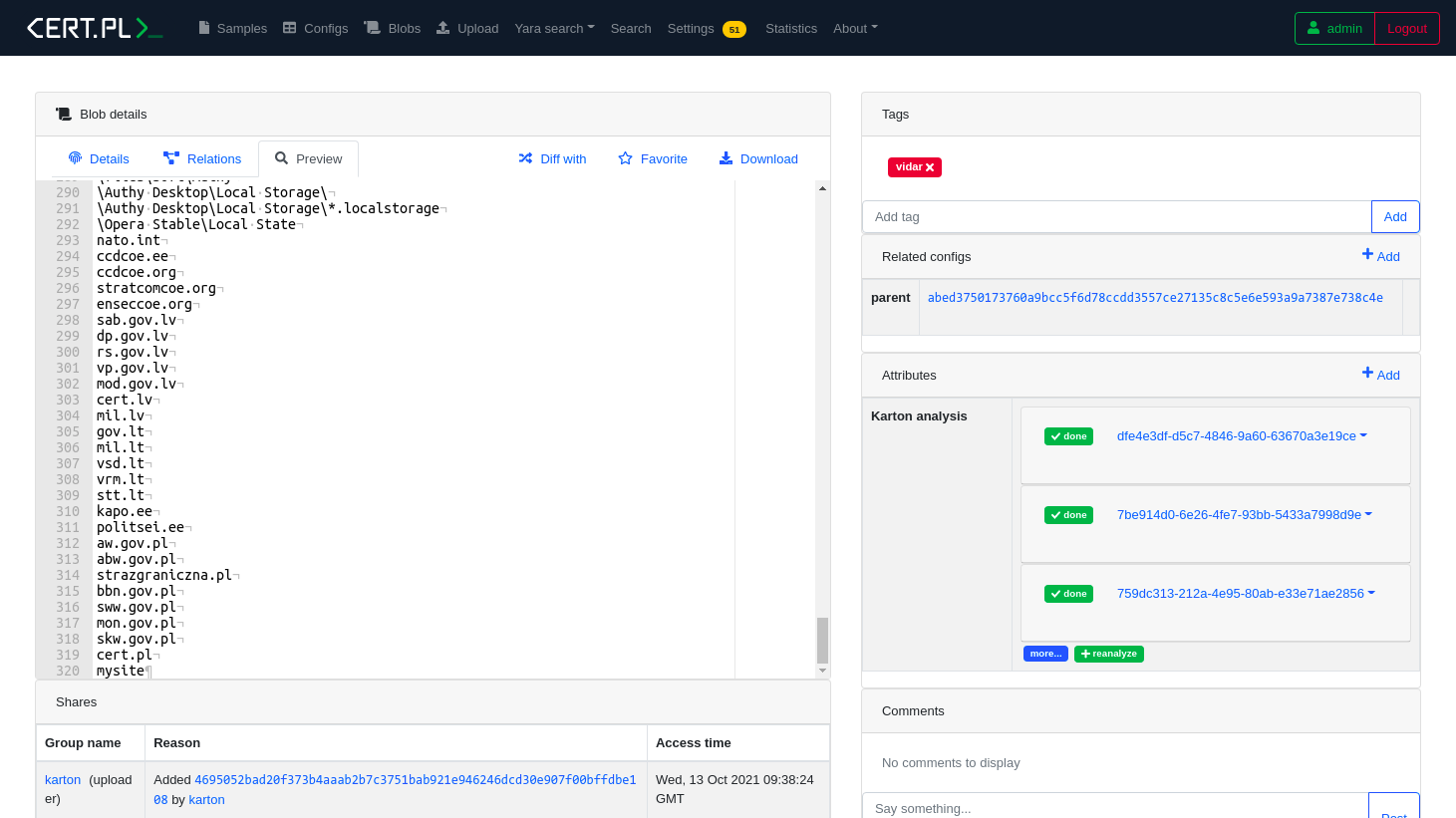 Automatically extracted strings from a Vidar sample
Automatically extracted strings from a Vidar sample
List of targeted hostnames:
ccdcoe.ee
ccdcoe.org
stratcomcoe.org
enseccoe.org
sab.gov.lv
midd.gov.lv
dp.gov.lv
rs.gov.lv
vp.gov.lv
mod.gov.lv
cert.lv
mil.lv
gov.lt
mil.lt
vsd.lt
vrm.lt
stt.lt
kapo.ee
politsei.ee
aw.gov.pl
abw.gov.pl
strazgraniczna.pl
bbn.gov.pl
sww.gov.pl
mon.gov.pl
skw.gov.pl
cert.pl
Vidar Stealer
During this analyiss we'll be looking at sample b115531ef23c109fb58c392379b7f55eff11169e1317b263da60edd9ac98f6b1.
Vidar Stealer, as the name suggests, is a malware family that is designed to steal and exfiltrate user information. This includes data such as credentials, cryptocurrency wallets and browser cookies.
It's widely believed that the family evolved from Arkei Stealer - another infostealer with similar capabilities. There is an excellent blogpost1 by @fumik0_ describing the similarities and differences.
While previous versions of the malware used to have C&C server address hardcoded directly in the sample, these days, it uses a bit more novel approach where the address is fetched from a social media platform like FACEIT or Mastodon.
String decryption and usage
Let's see how the strings in question were extracted and what are the semantics behind their usage.
The encryption is pretty straightforward. Each blob is produced by xoring two static strings located in the .rdata section.
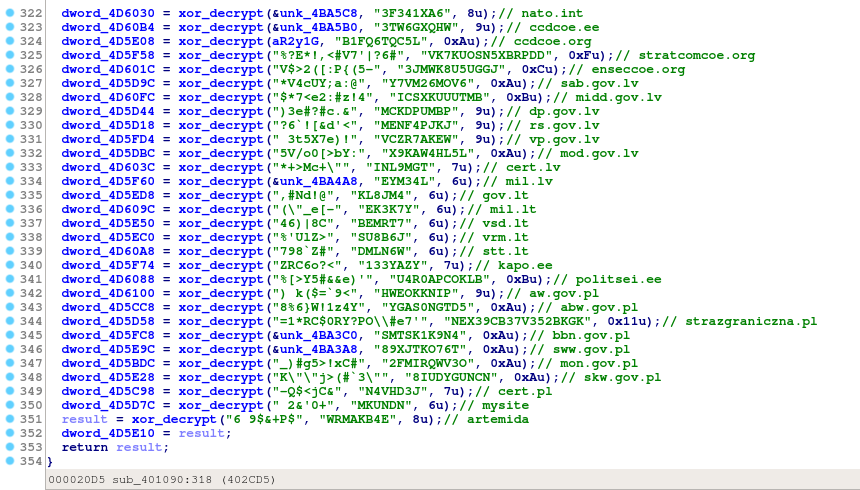 Xor string decryption
Xor string decryption
The decoded strings are then used in a subsequent section of the binary, where they are compared with hostnames of stolen credentials.
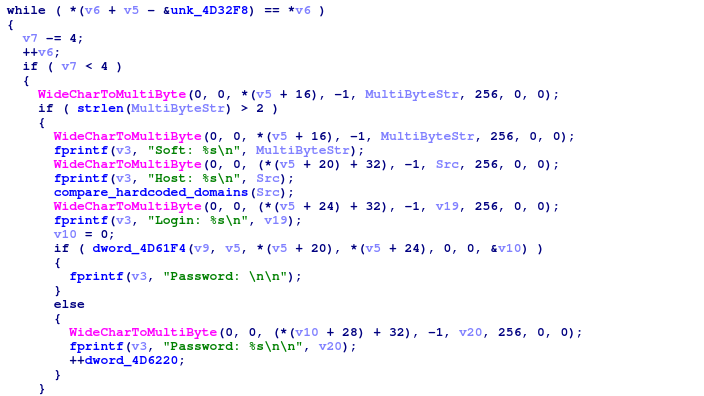 Iteration over stolen credentials
Iteration over stolen credentials
If at least one domain is matched, a global flag is incremented.
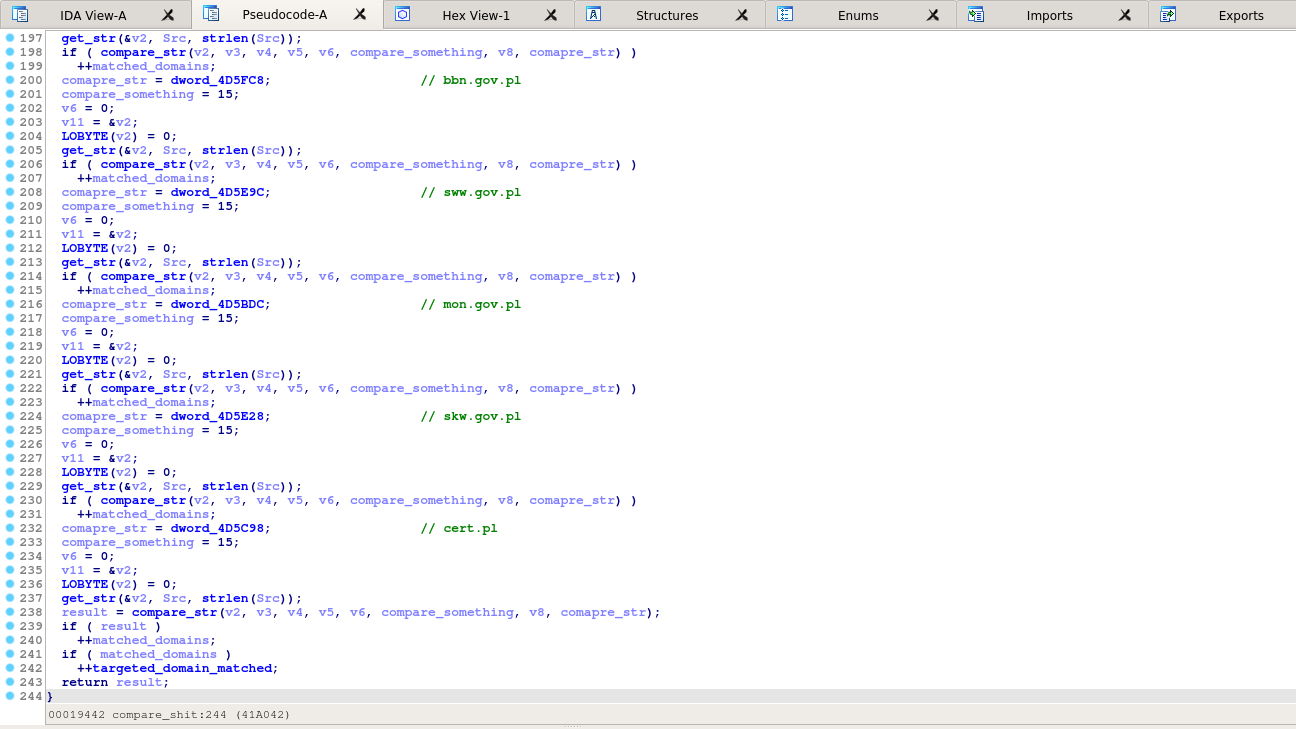 Hostname needle search
Hostname needle search
What's unusual about these Vidar samples is the use of a second C&C server responsible for handling credentials used when the global flag is set.
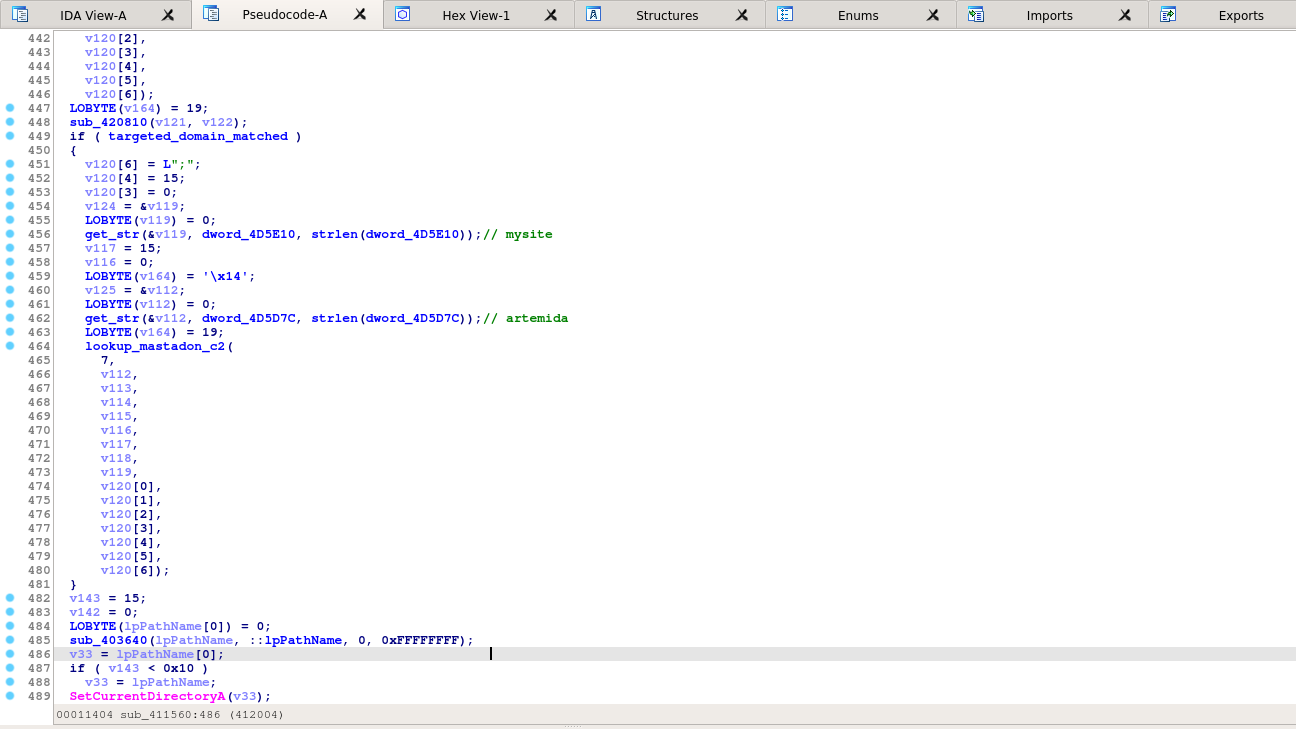 Alternative C&C server lookup
Alternative C&C server lookup
For the Vidar version analyzed, the C&C address is not stored directly in the sample but fetched from a specific user profile on the Mastodon platform.
In this specific sample, the default profile is @oleg98, and for reporting credentials from hosts of interest, @artemida is used.
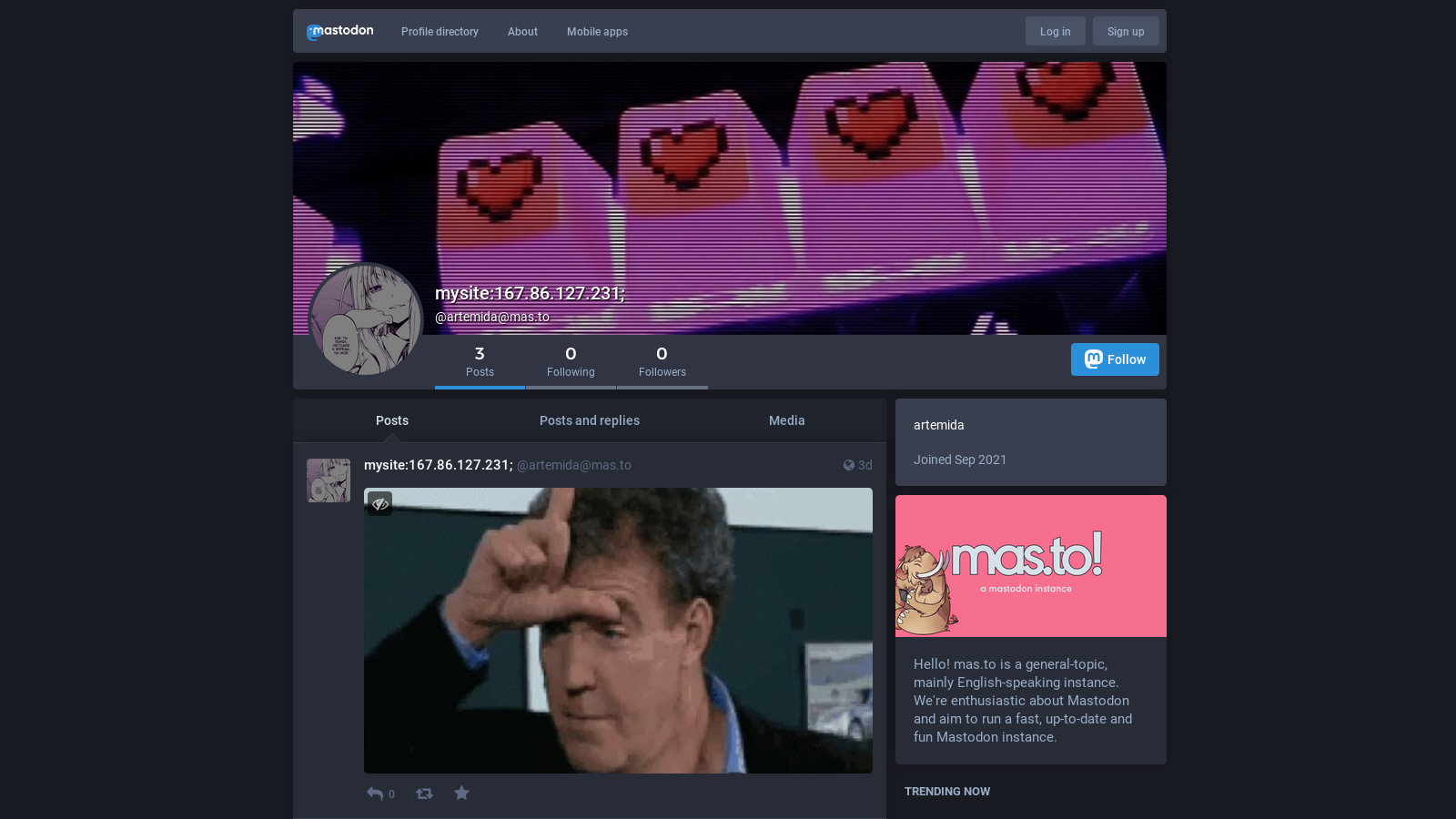 Mastadon artemida profile - pointing to
Mastadon artemida profile - pointing to 167.86.127.231
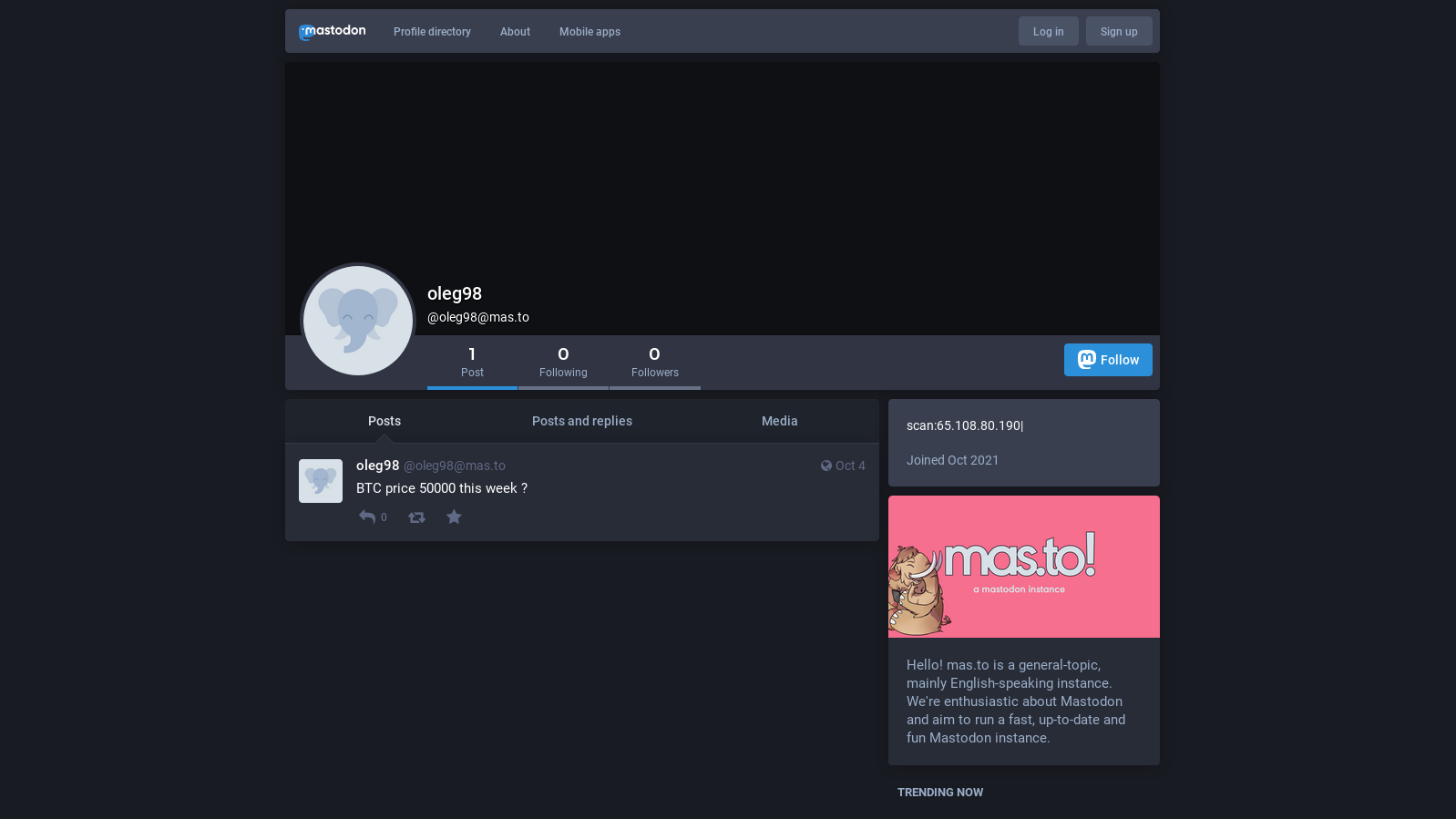 Mastadon oleg98 profile - pointing to
Mastadon oleg98 profile - pointing to 65.108.80.190
Campaign background
Unfortunately, we don't have much information on how the campaign was delivered and which entities were targeted directly. What is interesting, though, is that the actor used several other malware families.
Let's take a look at source samples in MWDB. We'll use mwdblib to quickly find the files that were extracted into the config in question.
mwdb search files 'child:(child:(config.dhash:abed3750173760a9bcc5f6d78ccdd3557ce27135c8c5e6e593a9a7387e738c4e))'
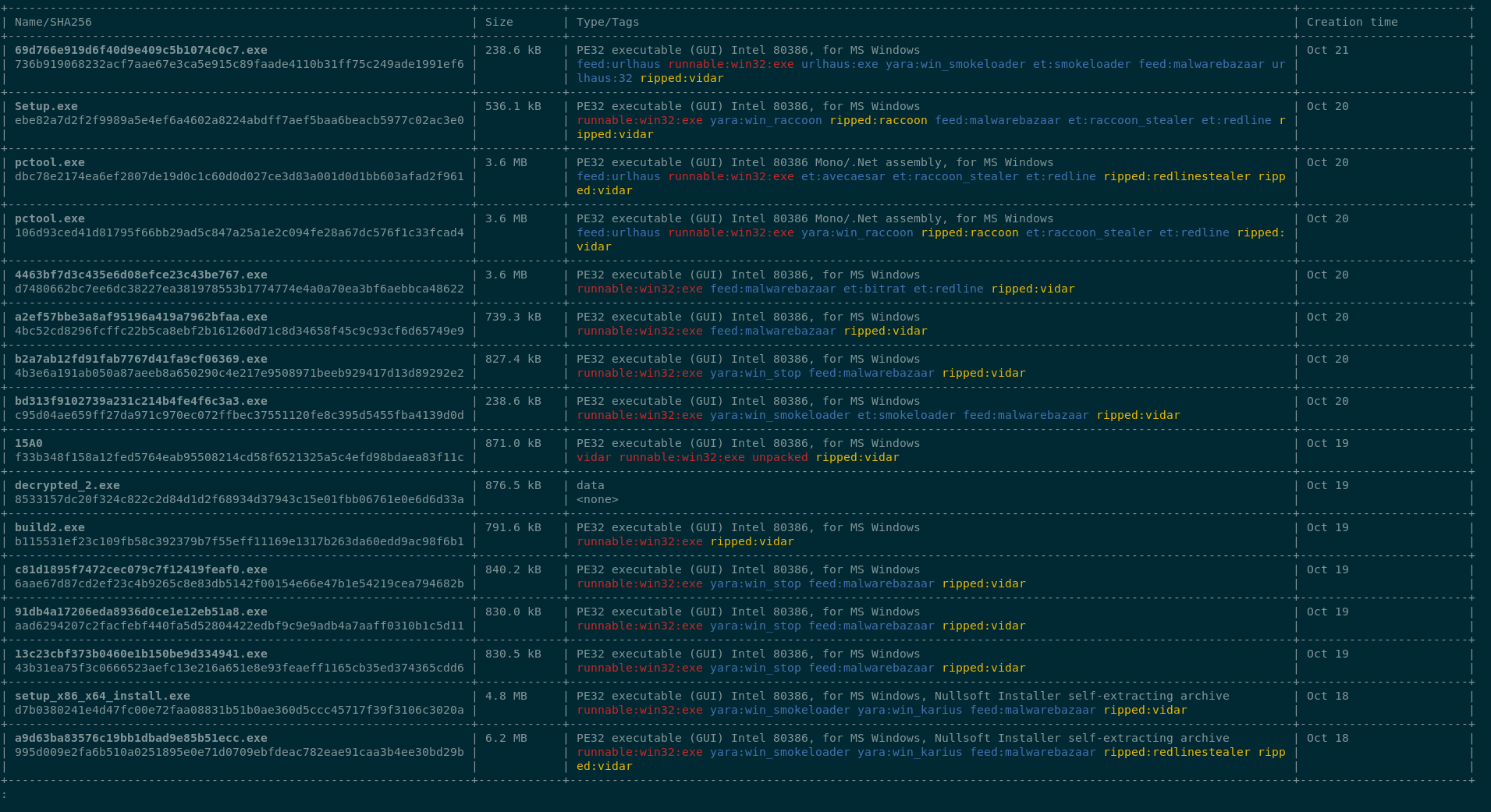
All matched samples and accompanying tags:
'77737d30b68a8fa75847570bfaa2c718875c532de61d7a5643504a1ac892a330', ['feed:malwarebazaar', 'ripped:raccoon', 'ripped:vidar', 'runnable:win32:exe', 'yara:win_karius', 'yara:win_raccoon', 'yara:win_smokeloader']
'9405f9084c8ec3eff442b83c20928fceb3e6372d504381b0527a7512a9889231', ['feed:malwarebazaar', 'feed:urlhaus', 'ripped:vidar', 'runnable:win32:exe', 'urlhaus:arkeistealer', 'urlhaus:exe']
'062c573497b73b4feaa77a78c2c76f6b095e51de635ac936e034f72afa081ecf', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe', 'yara:win_stop']
'c8aa42e07176d24c933d1e2bc4f0052b2973f98fc6e395d90f09e07dbf7c0585', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe']
'736b919068232acf7aae67e3ca5e915c89faade4110b31ff75c249ade1991ef6', ['et:smokeloader', 'feed:malwarebazaar', 'feed:urlhaus', 'ripped:vidar', 'runnable:win32:exe', 'urlhaus:32', 'urlhaus:exe', 'yara:win_smokeloader']
'ebe82a7d2f2f9989a5e4ef6a4602a8224abdff7aef5baa6beacb5977c02ac3e0', ['et:raccoon_stealer', 'et:redline', 'feed:malwarebazaar', 'ripped:raccoon', 'ripped:vidar', 'runnable:win32:exe', 'yara:win_raccoon']
'dbc78e2174ea6ef2807de19d0c1c60d0d027ce3d83a001d0d1bb603afad2f961', ['et:avecaesar', 'et:raccoon_stealer', 'et:redline', 'feed:urlhaus', 'ripped:redlinestealer', 'ripped:vidar', 'runnable:win32:exe']
'106d93ced41d81795f66bb29ad5c847a25a1e2c094fe28a67dc576f1c33fcad4', ['et:raccoon_stealer', 'et:redline', 'feed:urlhaus', 'ripped:raccoon', 'ripped:vidar', 'runnable:win32:exe', 'yara:win_raccoon']
'd7480662bc7ee6dc38227ea381978553b1774774e4a0a70ea3bf6aebbca48622', ['et:bitrat', 'et:redline', 'feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe']
'4bc52cd8296fcffc22b5ca8ebf2b161260d71c8d34658f45c9c93cf6d65749e9', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe']
'4b3e6a191ab050a87aeeb8a650290c4e217e9508971beeb929417d13d89292e2', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe', 'yara:win_stop']
'c95d04ae659ff27da971c970ec072ffbec37551120fe8c395d5455fba4139d0d', ['et:smokeloader', 'feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe', 'yara:win_smokeloader']
'6aae67d87cd2ef23c4b9265c8e83db5142f00154e66e47b1e54219cea794682b', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe', 'yara:win_stop']
'aad6294207c2facfebf440fa5d52804422edbf9c9e9adb4a7aaff0310b1c5d11', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe', 'yara:win_stop']
'43b31ea75f3c0666523aefc13e216a651e8e93feaeff1165cb35ed374365cdd6', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe', 'yara:win_stop']
'd7b0380241e4d47fc00e72faa08831b51b0ae360d5ccc45717f39f3106c3020a', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe', 'yara:win_karius', 'yara:win_smokeloader']
'995d009e2fa6b510a0251895e0e71d0709ebfdeac782eae91caa3b4ee30bd29b', ['feed:malwarebazaar', 'ripped:redlinestealer', 'ripped:vidar', 'runnable:win32:exe', 'yara:win_karius', 'yara:win_smokeloader']
'6c2ad98af84288aff6f49ae92f9f71befbfaa4ac35d1a05b1441f1ce15124ee0', ['feed:malwarebazaar', 'ripped:raccoon', 'ripped:redlinestealer', 'ripped:vidar', 'runnable:win32:exe', 'yara:win_raccoon', 'yara:win_smokeloader', 'yara:win_stop']
'3276f5cb5545e19704b1ef2897c17d721d6e156323f48f19275997d3cc62d005', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe']
'ee6cb977e78651d7b9a3fd412a40f6e2cd1501f05b04c49e744db35c83181132', ['et:raccoon_stealer', 'et:redline', 'feed:malwarebazaar', 'ripped:raccoon', 'ripped:redlinestealer', 'ripped:vidar', 'runnable:win32:exe', 'yara:win_raccoon', 'yara:win_smokeloader']
'22dbf29f7b7ee63da9418ab462b83e242823b83af7d697e7cf34796febc4d884', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe']
'149d9555994e5930d863674a2c55d295d5a19446bed86ef1079ccbbbdae9975f', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe']
'90618d3aa5146d27b46476a4c7bfcc2e5323b74dcbcf2c0af6b4f00c4c2d9297', ['et:raccoon_stealer', 'et:redline', 'feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe']
'7a5444f5316764d3960132052abe097784a29b7390e0ece10c86b804c125100f', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe']
'98ee19dbbe959081f2d95b7f56af58fcb7ecdc5b85bb9ee13775376b9bad1ccf', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe']
'9fefd930a1cc7b257fe5a65bc3eda3167bc0f82895f288fc34eaca3411b2688b', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe']
'11a83b7f651c007cef7ca9490fc560dbfda8cd6b538199e277047c8087c7cee0', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe', 'yara:win_stop']
'611796a36903059a2d1725d7849a375b9aa2902254c0d5f5fa2122e83570ea3a', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe']
'7ec5f24e6f59719e6c071ec719dcfcbe8e48f5293f493b903f19446c1815048b', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe']
'518e682b4f0226db5e1abb7b62a32a2f46db719b6c407317273cbef56c811657', ['feed:urlhaus', 'ripped:vidar', 'runnable:win32:exe', 'urlhaus:arkeistealer', 'urlhaus:exe']
'bf4d1dcd4b9129f47ec4239fa5a33e00c981e5fac5b8be880b76d2a1f5753c34', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe']
'd9b6823ca8e13b78c269c5d21e948dbab625ea87d3370d163eeabeb3822aef56', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe']
'8a2abfa467352b278a1233aead9dffbb23a6d17bd50fe22e275ca92a1911c23c', ['feed:urlhaus', 'ripped:vidar', 'runnable:win32:exe', 'urlhaus:arkeistealer', 'urlhaus:exe']
'1fbbaa6cfa20d6e11a3e5e4ba0702f608d474cbf5a86eef891fb57a671c684be', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe']
'2692f4594cebfa3afca882274dc1432fea1ccbc7d3f37db3e15059722db1d97b', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe']
'9cffbade290f88c34b8a5e2e551fd9ae035eeda9d49d0eb0fecec8e40ecf2e84', ['feed:malwarebazaar', 'ripped:vidar', 'runnable:win32:exe']
We can see that besides Vidar, MWDB was also able to detect and extract configurations from the following malware families:
- Raccoon
- RedLine Stealer
- SmokeLoader
- STOP ransomware
All of the recognized samples were uploaded as a part of the URLhaus2, and MalwareBazaar3 feeds, both developed by abuse.ch.
Indicators of Compromise
C&C profile proxies
- hxxps://mas.to/@sslam
- hxxps://mas.to/@serg4325
- hxxps://mas.to/@xeroxxx
- hxxps://mas.to/@oleg98
- hxxps://mas.to/@artemida
C&C servers
- 65.108.80[.]190
- 167.86.127[.]231
Samples
16c3f8999141beee55afdb49670b9e44b4916816faeb643639a7ace81c13806a
1d4ecd52ab85b7f5229f00ee10d438286e361d4c304000abca8b3dcbe1d7c720
77737d30b68a8fa75847570bfaa2c718875c532de61d7a5643504a1ac892a330
9405f9084c8ec3eff442b83c20928fceb3e6372d504381b0527a7512a9889231
062c573497b73b4feaa77a78c2c76f6b095e51de635ac936e034f72afa081ecf
c8aa42e07176d24c933d1e2bc4f0052b2973f98fc6e395d90f09e07dbf7c0585
736b919068232acf7aae67e3ca5e915c89faade4110b31ff75c249ade1991ef6
ebe82a7d2f2f9989a5e4ef6a4602a8224abdff7aef5baa6beacb5977c02ac3e0
dbc78e2174ea6ef2807de19d0c1c60d0d027ce3d83a001d0d1bb603afad2f961
106d93ced41d81795f66bb29ad5c847a25a1e2c094fe28a67dc576f1c33fcad4
d7480662bc7ee6dc38227ea381978553b1774774e4a0a70ea3bf6aebbca48622
4bc52cd8296fcffc22b5ca8ebf2b161260d71c8d34658f45c9c93cf6d65749e9
4b3e6a191ab050a87aeeb8a650290c4e217e9508971beeb929417d13d89292e2
c95d04ae659ff27da971c970ec072ffbec37551120fe8c395d5455fba4139d0d
6aae67d87cd2ef23c4b9265c8e83db5142f00154e66e47b1e54219cea794682b
aad6294207c2facfebf440fa5d52804422edbf9c9e9adb4a7aaff0310b1c5d11
43b31ea75f3c0666523aefc13e216a651e8e93feaeff1165cb35ed374365cdd6
d7b0380241e4d47fc00e72faa08831b51b0ae360d5ccc45717f39f3106c3020a
995d009e2fa6b510a0251895e0e71d0709ebfdeac782eae91caa3b4ee30bd29b
6c2ad98af84288aff6f49ae92f9f71befbfaa4ac35d1a05b1441f1ce15124ee0
3276f5cb5545e19704b1ef2897c17d721d6e156323f48f19275997d3cc62d005
ee6cb977e78651d7b9a3fd412a40f6e2cd1501f05b04c49e744db35c83181132
22dbf29f7b7ee63da9418ab462b83e242823b83af7d697e7cf34796febc4d884
149d9555994e5930d863674a2c55d295d5a19446bed86ef1079ccbbbdae9975f
90618d3aa5146d27b46476a4c7bfcc2e5323b74dcbcf2c0af6b4f00c4c2d9297
7a5444f5316764d3960132052abe097784a29b7390e0ece10c86b804c125100f
98ee19dbbe959081f2d95b7f56af58fcb7ecdc5b85bb9ee13775376b9bad1ccf
9fefd930a1cc7b257fe5a65bc3eda3167bc0f82895f288fc34eaca3411b2688b
11a83b7f651c007cef7ca9490fc560dbfda8cd6b538199e277047c8087c7cee0
611796a36903059a2d1725d7849a375b9aa2902254c0d5f5fa2122e83570ea3a
7ec5f24e6f59719e6c071ec719dcfcbe8e48f5293f493b903f19446c1815048b
518e682b4f0226db5e1abb7b62a32a2f46db719b6c407317273cbef56c811657
bf4d1dcd4b9129f47ec4239fa5a33e00c981e5fac5b8be880b76d2a1f5753c34
d9b6823ca8e13b78c269c5d21e948dbab625ea87d3370d163eeabeb3822aef56
8a2abfa467352b278a1233aead9dffbb23a6d17bd50fe22e275ca92a1911c23c
1fbbaa6cfa20d6e11a3e5e4ba0702f608d474cbf5a86eef891fb57a671c684be
2692f4594cebfa3afca882274dc1432fea1ccbc7d3f37db3e15059722db1d97b
9cffbade290f88c34b8a5e2e551fd9ae035eeda9d49d0eb0fecec8e40ecf2e84
446d53cdc62a86025835e93938afeb9c1b24f28f2bade4980c01ac517b76c760
