
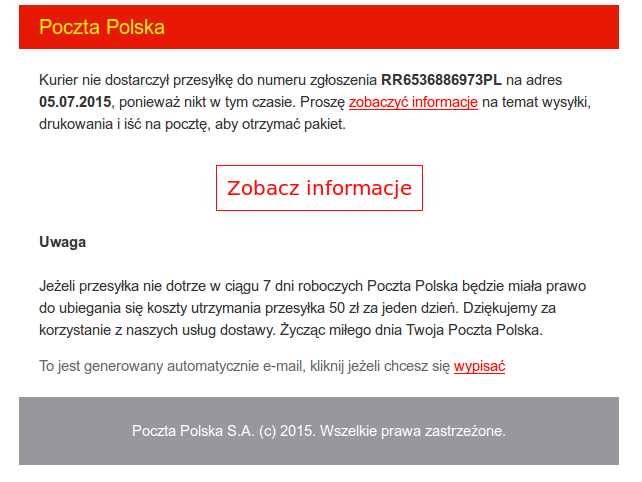
On the 7th of May, 2015 we observed a new malicious e-mail campaign, which used the logo and the name of Polish Post Office (”Poczta Polska”). The e-mail supposedly informed about an undelivered package – however, they also included a link which, after several redirects, lead to the download of a malicious file. This file was either a Windows executable or Android APK file (depending on the presented User Agent string).
The e-mails were similar to the one presented below.
Ransomware for Windows
If we visited the link from the e-mail using a Windows browser we were redirected to a website that asked to provide a CAPTCHA code and, when successfully verified, presented you with an exe file. The website informed that this is just a “PDF” file that you have to present at the post office in order to receive the package. This website is presented at the screenshot below. The executable file was really a TorrentLocker ransomware, which encrypted user files and demanded ransom for the decrypter.
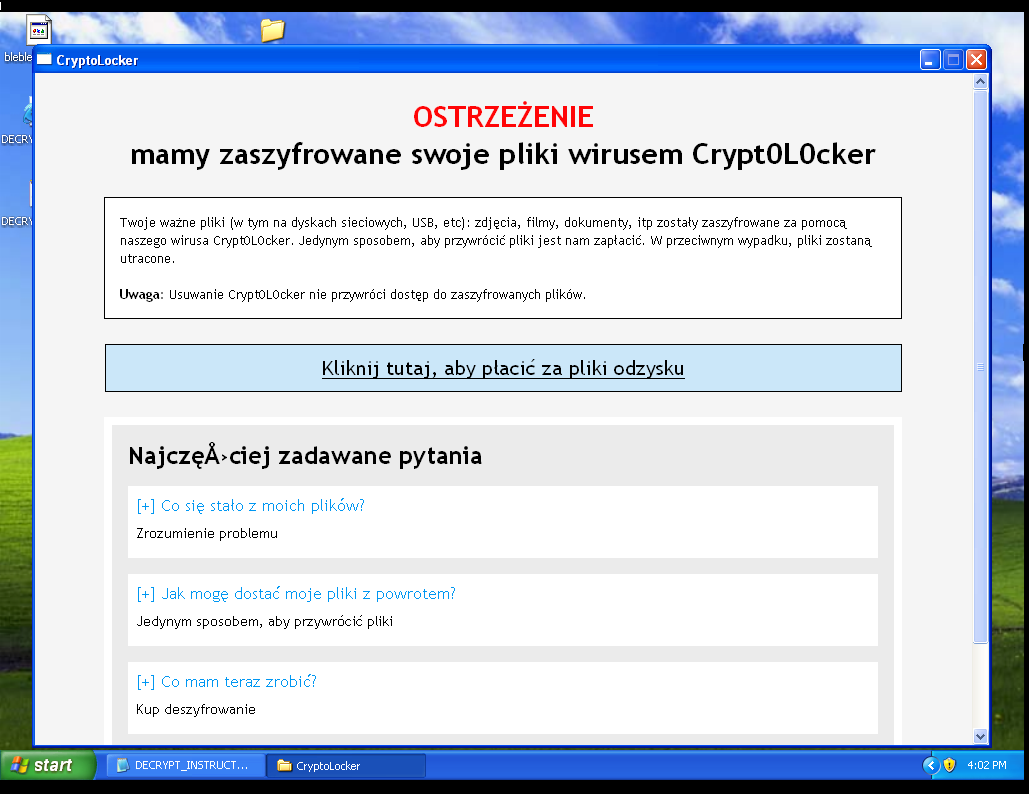
After the ransomware encrypts users files it displays a window presented below. It informs users about the encryption and what to do in order to decrypt the files. In order to buy the decryption software, the user must visit a Tor website, located in the
domain. Convieniently, several Tor web proxies are also provided, so that the user does not have to install the Tor browser.
In order to pay for the decrypting software you have to use Bitcoin and pay 1.47546 BTC (approximately 325 USD). However, if we we delay our decision for more than 4 days, we have to pay double that amount.
Malware on Android
If we were using Android browser to visit the link provided in the e-mail message, we were redirected to the page with an APK file and instructions on how to install it. In this case the provided reason was the same as with the Windows executable: you have to install the APK in order to track the package.
The installed malware receives commands either via SMS or using a hardcoded C&C URL. SMS commands have the following format:
Commands are only accepted if they are sent from a specified admin number. Some of the commands are listed below.
-
<span class="text">set_admin</span>
– change the admin number.
-
<span class="text">send_sms</span>
– send SMS to a specified number (e.g. to send Premium SMS).
-
<span class="text">send_fake</span>
– create a “fake” SMS message – it will be presented in the inbox, but it was not actually sent.
-
<span class="text">set_url</span>
– sets the URL of a new C&C.
-
<span class="text">wipe</span>
– resetting phone to factory settings. Also locks the screen with 12345 password.
-
<span class="text">get_ussd</span>
– sending the USSD code (checking prepaid phones balance).
This APK also allows the attackers to redirect incoming messages to a different number. If the messages are coming from the administrative number, the ringer sound is also muted so that user can miss this message.
The application is also really persistent when it comes to the device administrator privileges. If the user tries to revoke device administrator privileges, he succeeds but is then repeatedly asked for that permission. It gets to the point, that a user cannot use the mobile device and eventually clicks on “Accept”.
This malware also uses a technique called “Application overlay” – it displays a window on top of a running app asking for login and password. This way users are almost sure that it is a running app that is asking for this password. This is true for, e.g. GMail app, which is illustrated in the movie below. Notice the slight gap between the opening of the app main window and the login/password popup.
It’s worth noticing that in the case of this app, attackers do not need a computer malware counterpart to transfer funds from the victim’s account. By taking control of the user messages, they have access to the SMS-based one time password. By using the “application overlay” technique they can also get the user to send login and password details. So, by attacking only a user’s phone they gain almost complete control over user’s bank accounts.
Summary
It seems more and more certain that malicious multiplatform solutions are the future of cyberattacks. This approach can provide the attacking group with a larger number of entry points – whether it is a “regular” user, who reads e-mail on his computer, or a more mobile user, that uses Android to read his e-mails. On the other hand, this is also a slight overhead for the attackers – they have to manage two distinct malware families on different operating systems. Maybe in the future there will be kits, which will combine all infected devices in one C&C panel – no matter if the device is phone, computer, tablet or even a car. This approach can lead to a bigger success of malicious campaigns, as users are using different means more and more to read e-mails and connect to the Internet.
MD5 fingerprints of the analyzed files
e83d83761416742ab69baf379f2b34dd ransom.exe (Windows)
