 In the last few days the most popular vulnerability seems to be CVE-2014-0160. This two years old vulnerability was in OpenSSL library, versions 1.0.1a-f, and allows to read a part of the memory of the process. The use of this library is very prevalent not only in the server environments (e.g. WWW, or mail), but also on desktops in some client applications. However, the most popular browsers are not affected in any way. We publish our analysis of this CVE and its effect on TOR and Polish network. Information on the Electronic Frontier Foundation Deeplinks blog allows to speculate that the intelligence agencies knew about the bug a year ago and actually used it.
In the last few days the most popular vulnerability seems to be CVE-2014-0160. This two years old vulnerability was in OpenSSL library, versions 1.0.1a-f, and allows to read a part of the memory of the process. The use of this library is very prevalent not only in the server environments (e.g. WWW, or mail), but also on desktops in some client applications. However, the most popular browsers are not affected in any way. We publish our analysis of this CVE and its effect on TOR and Polish network. Information on the Electronic Frontier Foundation Deeplinks blog allows to speculate that the intelligence agencies knew about the bug a year ago and actually used it.
What is CVE-2014-0160 and how to prevent its exploitation?
This vulnerability is present in the OpenSSL library, so users need to update it to at least 1.0.1g (or patch an existing one). Some older versions of this library are not vulnerable. However, this update is not sufficient. Restart of the affected services is also needed, in order to load an updated version of the library.
Some products link OpenSSL library statically. If this is a case for you, you have two choices. You can recompile the affected service or, if you do not have the source code, wait for the software vendor to update its product.
How bad is it?
This vulnerability allows to read a part of the memory of the process that uses the OpenSSL library. This part of memory can contain various data. We have tested a couple of services to see what exactly can be accessed. The web interface of the Zimbra mail server returned snippets of e-mail messages, as the one pictured below.
<b>Do: </b>\”xxx\” <[email protected]><br>
<b>Wys\u0142ane: </b>wtorek, 4 luty 2014 12:57:30<br>
< b>Temat: </b>Re: test<br>
<div><br>
</div>plik<br> —– Original Message —– <br>
From: \”xxx\” <[email protected]><br>
To: <[email protected]><br>
Sent: Tuesday, February 04, 2014 12:30 PM<br>
Subject: test<br><div><br>
</div><br>
> Hello,<br>
><br>
><br>
> 123<br>
><br>
><br>
> Najlepsze \u017cyczenia.<br>
><br>> <br>
</div><div><br>
</div></div></body></html>”}},
{“ci”:”xxx@zimbra”,
“attach”:{“mp”:[{“mid”:”262″,
“part”: “2.2”}]}}]}]}],
“irt”:{“_content”:”<[email protected]>”}}}
Of course, there was a lot of different mails contained in the dumped memory. Apart from the e-mail messages, a cookie contents were also returned (like
). We recommend to check your mail servers for this bug.
Also SSL-VPN gateways are vulnerable to this bug. Companies should upgrade their SSL-VPN gateways and also remind their employees to update their client software. We have tested Fortigate with FortiOS version 5.0 B0252 (GA Patch 5) and we were able to retrieve login and password. Fortinet has released FortiOS update to version 5.0.7 B3608. The data leak is presented below.
00d0: 10 00 11 00 23 00 00 00 0F 00 01 01 08 70 2A 66 ….#……..p*f
00e0: 4D 6B 5C BB E1 F7 80 DD B9 FE 1C 04 04 04 04 04 Mk\………….
00f0: 0A 0D 0A E 61 6D 65 3D 6B 61 6D 69 …username=kami
0100: 6C 26 63 72 65 64 65 6E 74 69 61 6C 3D 74 65 73 l&credential=tes
0110: 74 70 61 73 73 77 64 26 6A 75 73 74 5F 6C 6F 67 tpasswd&just_log
0120: 67 65 64 5F 69 6E 3D 31 26 72 65 64 69 72 3D 25 ged_in=1&redir=%
0130: D 6F 74 65 25 32 46 69 6E 64 65 78 2Fremote%2Findex
0140: 26 61 6A 61 78 3D 31 BE D6 95 3C 0B 3E BE DE FA &ajax=1…<.>…
0150: 71 AD 40 61 90 6B 1E F0 A9 AC 43 04 04 04 04 04 [email protected]….C…..
0160: AA 87 29 0F D7 44 9B 8B C4 9B 06 F1 4F DB 01 01 ..)..D……O…
Another example, that we have studied, were the TOR network servers. Some of the servers returned parts of configuration files, like PGP public keys or administrator’s e-mail. This is of course already available, so may not be considered as a leak. However, due to the different memory layout, sometimes it may contain a private key, but we were unable to obtain such information. We were able to obtain parts of server configuration (e.g.
and so on) or lines from a log file:
Also, visited domain names, snippets of the HTML or even snippets of the HTTP requests are available. These are just examples of the data that can be obtained.
What is more, TOR servers are really easy target for this CVE. There are publicly available lists of TOR servers, including their uptime. Those servers that have high uptime are, most probably, not patched and will leak memory.
We scanned TOR network on 9th of April and, out of 5174 scanned hosts:
- 1088 was vulnerable,
- 2916 was not vulnerable.
- 970 was vulnerable,
- 2926 was not vulnerable.
- login data (login and password),
- server configuration (e.g. .htaccess files)
- 15737 were vulnerable, which is 1.8%,
- 675478 were not vulnerable, which is 76.8%.
Rest of the servers did not reply or reported an error.
On 10th of April out of 4960 scanned hosts:
Apart from these data we also received reports concernig a leak of:
How is the Polish network affected?
We scanned Polish IPs (or at least a list of Polish IPs that is publicly available), which had 443/tcp port opened, and the results are presented below.
Rest of the IPs either did not respond or returned an error. The most popular domain seems to be
.
Out of 13490 the most popular
domains (according to alexa) 765 (5.7%) are vulnerable, including some large e-shops.
Our ARAKIS system observed an increased activity on the following TCP ports that are frequently used with SSL: 443 (HTTPS), 465 (SMTPS), 993 (IMAP), 995 (POP3). Graphs are presented below.
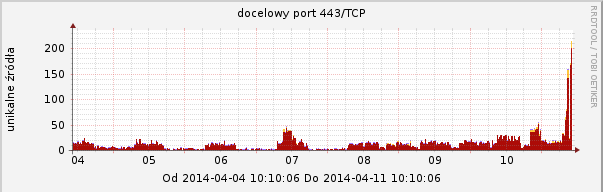
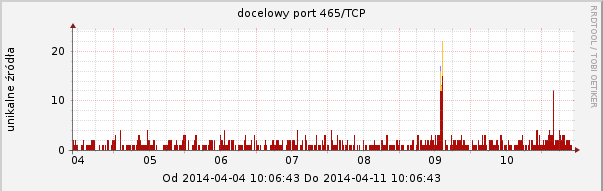
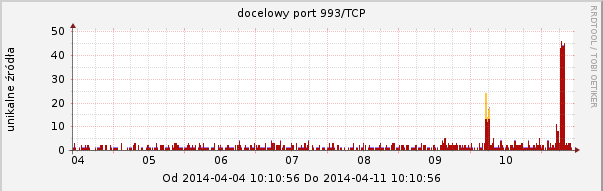
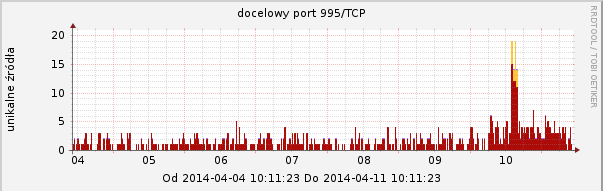
Recommendations
We recommend update of the OpenSSL library update and restart of all related services. In order to be even more secure, administrators should revoke certificates they used to encrypt connections and authenticate users. Users, on the other hand, should change all of the passwords that could be transferred via SSL, just to be on the safe side.
Summary
In this article, we were mainly concerned with affected servers. However, client side applications can also be affected if they use the vulnerable OpenSSL version. The attacker can extract information from the client software. It is as simple as making the user connect to the server controlled by the attacker.
This error is of course very serious, however, we still do not have any information about tools that can be used to extract a non-random part of the process memory. We advise users to update OpenSSL library and restart all services that use it. You can check if your website is vulnerable using this online scanner.
