 On the 31st of October Google released a new version of the Android Operating System – 4.4 called KitKat. This version introduces a number of new features, including a handful of security improvements. It also introduces a new approach to SMS and MMS handling, which breaks the compatibility of some Android malware and makes it easier for users to spot a malware infection. This security improvement comes as a side effect to the new system-wide approach to messaging applications.
On the 31st of October Google released a new version of the Android Operating System – 4.4 called KitKat. This version introduces a number of new features, including a handful of security improvements. It also introduces a new approach to SMS and MMS handling, which breaks the compatibility of some Android malware and makes it easier for users to spot a malware infection. This security improvement comes as a side effect to the new system-wide approach to messaging applications.
One app to rule them all
KitKat brings a new intent:
. This intent is meant to be used when the application wants to receive all text messages right after they have been delivered. This means that, in order to hide message from the user, malware must declare this Intent. However, only one application in the whole operating system can receive this action – the one declared the default messaging application. In the SDK version of Android 4.4 this is the usual system messaging application.
Intent
is still present – however this is now reserved for the application that want to read incoming messages. This application cannot interfere with the message text or hide the message from the user. This difference is illustrated on the diagram below – left side shows Android 4.3 and right side is the new Android 4.4.
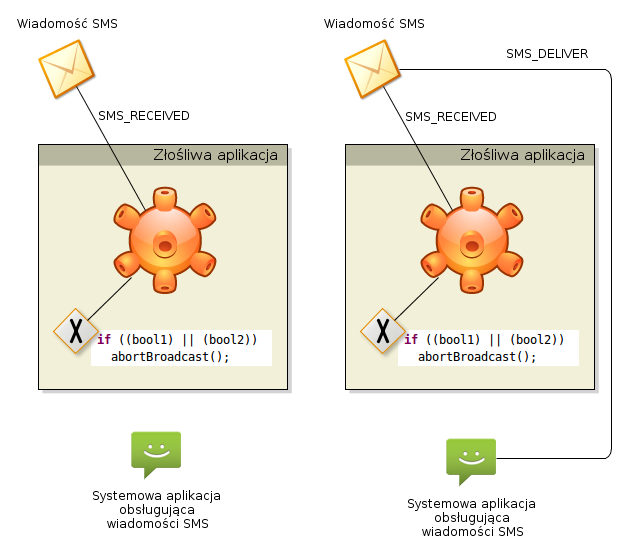
Intent was introduced for this purpose.
All sent messages are also passed to the default system application and saved by it. This means that the malware cannot hide sent messages and we can easily determine whether our phone has been infected or not. This, however, is not true with the MMS messages. The non-default application also cannot delete, save draft or mark message as read.
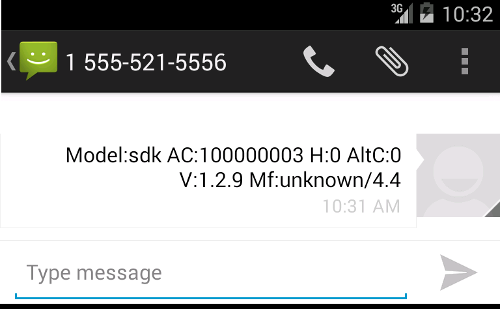
Because of this, a user should always pay attention to her inbox and sent messages. If you find any suspicious message, this may be a sign of malware infection. For example, previously described E-security application leaves the following saved in the sent messages:
Time to get serious with SELinux
Previous Android version had SELinux (Security-Enhanced Linux) module already included in the kernel. However, in order to keep backward compatibility, it was set in the permissive mode. This mode only logs the policy violations, but does not prevent them. Android KitKat comes with SELinux in enforcing mode, which enforces policies. Your SELinux mode can be easily checked using the following command.
|
1
2 |
$ adb shell getenforce
Enforcing |
Previous Android version also enabled SELinux mode change, if the user had access to the administrative account. A very interesting series of articles discussing the Android SELinux can be found on securityblog.org. It also contains an example of exploit prevented by the use of SELinux.
Google Certificate Pinning and custom SSL CA notifications
SSL connections have two additional security features. In order to prevent man-in-the-middle attacks, users are now notified about the custom Certificate Authority certificate used by the SSL connection, even if it is installed on their device. The man-in-the-middle attack can also be used in all kind of webfilters, which want to analyze the page content returned to the user. Second feature is the certificate pinning for Google services. This means that you cannot connect to Google services using any valid certificate – you have to use the one that is saved in the operating system.
Extras: ECDSA and FORTIFY_SOURCE
Android KitKat was compiled using the
compiler flag. That means that the compiler tried to prevent some cases of buffer overflow – the ones that can be prevented automatically during the compilation.
KitKat also supports ECDSA keys, which means that you can use Elliptic Curve cryptography for signing. This extends the cryptographic algorithms and may lead to a slower key size increase than in, e.g. RSA algorithm.
Summary
Despite the changes being more evolution than revolution, they are small steps in the direction of the secure operating system. A default messaging application means a compatibility problems for some of the SMS based malware and makes it easier for researchers to search for malware infection signs, making it also harder for cybercriminals to write new malware. Now they would have to change the default messaging application in order to hide C&C messages from users. While SELinux and other features improve the OS security, they do not prevent the most common infection vector today – installing application from unverified sources and accepting its, sometimes very invasive, privileges.
There is another problem with this security enhancements. Because of the heterogeneity of Android environment, OS upgrade depends mainly on the phone manufactures. KitKat will most probably reach only new or high-end phones, which will exclude a part of Android users, e.g. those, whose phones fall out of the traditional 18-month update window.
