
iBanking malware was already described on our blog in connection with the attacks targeting Polish e-banking users at the end of 2013. This malware posed as a mobile antivirus application, while in reality it was use to steal one time passwords that were sent via text message. The attack scenario is very similar to the ones observed in the past, seen not only in Poland, but also in other countries. However, this time attackers also used QR codes, which are supposed to be more convenient for users then sending the app URL over the SMS.
Attack scenario
First, the user must visit an e-banking website from the infected machine. The machine is first infected with malware that supports “webinjects”, i.e. small JavaScript snippets that are injected to the website code. When a user logs into his account, the JavaScript renders a message similar to the one below (in Polish).
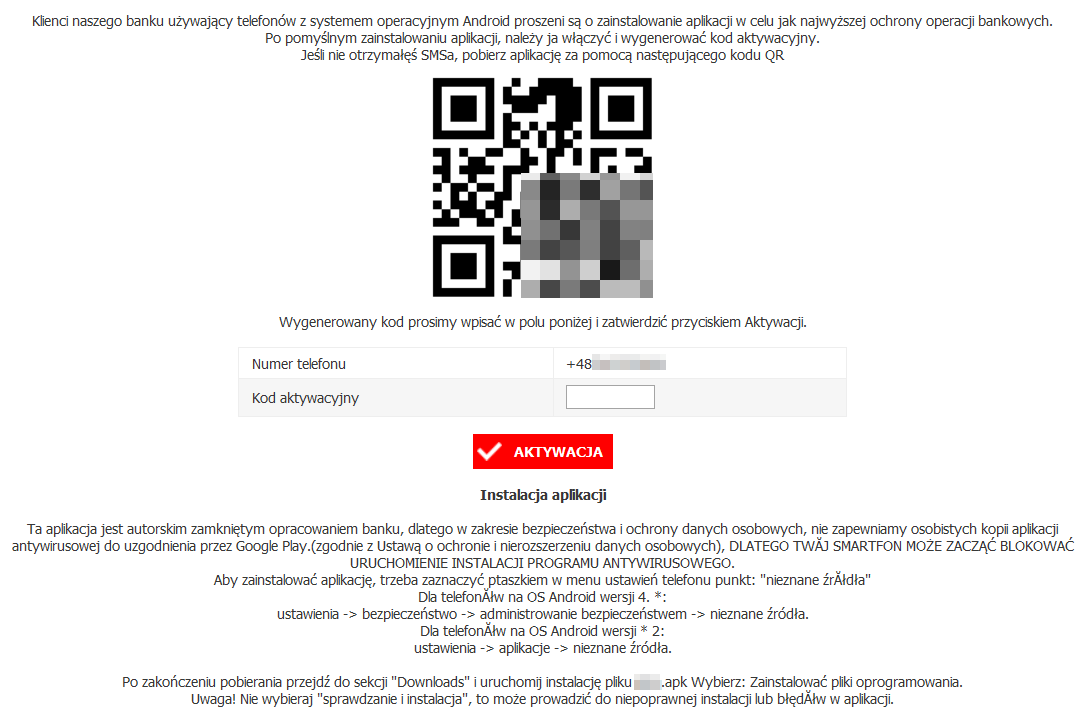
This message persuades user that the bank has prepared an app that allows for “the highest security” when dealing with the e-banking service. The message contains both the QR code and sends a text message, so that a user can conveniently choose a method of infection. The message also contains instructions to enable installation from untrusted sources, because the malware cannot be installed from Google Play. It also mentions antivirus software and the fact that it can produce a “false positive” when scanning the app.
- redirect phone calls,
- eavesdrop using the phone’s microphone,
- reset the mobile phone to factory default, effectively making the forensic analysis harder.
When a user downloads and installs the iBanking app, the attackers gains total control of the mobile phone and can:
The main window of the application is similar to the one presented below.
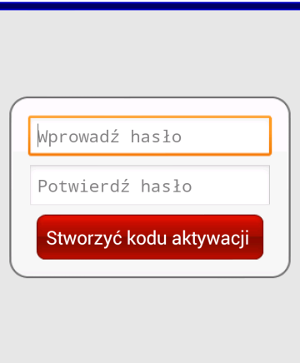
It does not matter what password is entered in the app – the attacker already has a login and a password from the infected machine.
Summary and recommendations
Be cautious when you see any suspicious or unusual messages in your e-banking service. If you have any doubts, contact your bank. Especially when you are asked to provide one time password for an operation that you did not perform. Always install apps from trusted sources, like Google Play and do not allow excessive privileges to any app. If you are already infected follow the steps outlined in the May 2014 issue of OUCH! Security Awareness Newsletter: I’m Hacked, Now What?.
