
Yesterday Polish security portal, Niebezpiecznik.pl, has informed about a new kind of malware spreading through Facebook (article in Polish). CERT Polska got a sample of this malicious software to analyse. Despite Facebook being not a new attack vector, this malware sample is very interesting. Currently it is detected by some antiviruses, but not even a majority. Additionally, this malware is protected against both debugging and network traffic analysis. In order to protect binary code from reverse engineering, it was obfuscated using a special Protector. Network traffic is encrypted (even the DNS queries!) and produced in excess.
Niebezpiecznik.pl provided following VirusTotal results for this malware sample:
How does it spread?
Our analysis showed that malware can spread in a three, very social, ways. Firstly, it spreads through Facebook, writing a chat short chat message and posting following message on a wall:
|
1
|
http://xxxxxxxx.com/xxxxxxxx.php?ref=facebook&w=[random characters]&resource=youtube&w=[name] :* favourite [random characters] 😀
|
Secondly, it sends a following Skype message:
|
1
|
youtube favourite [random characters]! http://xxxxxxxx.com/xxxxxxxx.php?ref=facebook&w=[random characters]&resource=youtube&w=[name]
|
Finally, it sends an MSN message:
|
1
|
:* http://xxxxxxxx.net/xxxxxxxx.php?ref=facebook&w=[random characters]&resource=youtube&w=[name] youtube hit [random characters] 😀
|
After clicking on one of the above links, malware is downloaded to the victim’s computer. Application icon suggests that it is a JPG image. If user has hidden file extensions (turned on by default), she can be persuaded to click on an application, thinking it is an image.
What is it doing?
Upon starting, malware sends a lot of DNS queries (over 70!) asking for different addresses, both of known services (e.g. goo.gl or tinyurl.com) and malicious sites, which will be used later to communicate with the C&C server. By doing so, it ensures that the C&C domain is present in the Windows DNS cache, so when malware asks for this domain again there is no evidence in the network traffic which server was used as a C&C. List of all domains is provided below.
abbrr.com
abe5.com
a.gd
ahref.in
alturl.com
a.nf
arm.in
awe.sm
b23.ru
b4it.net
bacn.me
beam.to
bit.ly
bitly.com
bloat.me
budurl.com
burnurl.com
canurl.com
checkshorturl.com
chilp.it
cjb.net
cli.gs
clockurl.com
co.nr
cowurl.com
cozyurl.com
d0g.me
dboost.de
decenturl.com
dfl8.me
digbig.com
digg.com
diggurl.com
doiop.com
durl.us
fff.to
fhurl.com
goo.gl
hotshorturl.com
is.gd
itoo.ws
ity.im
l9k.net
lilipala.com
liltinti.com
mo.by
nipurl.com
pralala.com
redir.ec
shortlink.se
shortswitch.com
shorturli.com
shorturli.net
shorturl.info
shorturli.org
snap.vu
su.pr
surf.to
ta.gg
tintiurl.com
tintiurl.net
tinyarrows.com
tiny.cc
tinylink.com
tinylink.in
tinylink.ir
tinylink.me
tinysong.com
tinyurl.com
tiny-url.org
unshorten.com
wong.to
x.nu
yep.it
yourls.org
yvy.me
Additionally, malicious software does not use the DNS answer directly. IP address retrieved from DNS is in some way “encrypted” and after decryption it is used for an encrypted HTTP communication with the C&C. This makes a network traffic analysis very difficult. Server sends a configuration to the malware which specifies, among other things, the way it should spread. Decrypted config, which our sample downloaded, is provided below.
dummy=1
dl=http://
dlid=0
qint=900000
pint=100
pcnt=1
hp=http://domredi.com/1/
hpid=116
kw=none
msn=:*
http://xxxxxxxx.net/xxxxxxxx.php?ref=facebook&w=%RAND1%&resource=youtube&w=%NAME%
youtube hit %RAND2% :D
msnseq=226
fbchat=:P
fbchatseq=0
fbwall=
http://xxxxxxxx.com/xxxxxxxx.php?ref=facebook&w=%RAND1%&resource=youtube&w=%NAME%
:* favourite %RAND2%! :D
fbwallseq=204
skype= youtube favourite %RAND3%!
http://xxxxxxxx.com/xxxxxxxx.php?ref=facebook&w=%RAND1%&resource=youtube&w=%NAME%
:D ahhahahaa
skypeseq=91
Configuration is decrypted (and encrypted) using the function below.
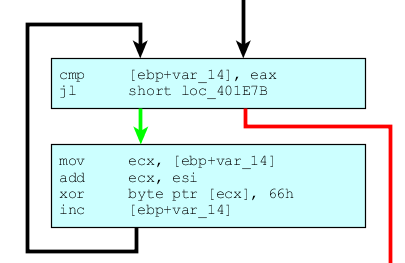
Victim’s computer is then used to spread the malware, using contacts from Facebook, Skype and MSN communicator using the links provided above. The
property is used to download additional malicious software and infect the computer with it. Additionaly, homepage of all major browsers is set to the value of
property using a function provided below.
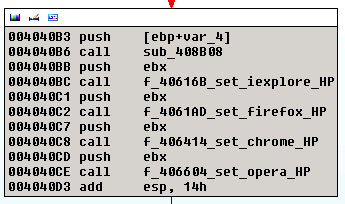
Malware also adds itself to the Windows autorun list.
Domains used to spread the malware are:
yrfotosonica.com
twipavideosonic.com
However, it should be noted that these malware domains are easily changable through configuration.
Non-standard use of DNS queries
This malware is exceptional in a way that it generates a lot of DNS traffic. Additionally, to retrieve the IP address of C&C it does not use the DNS response directly, rather decrypting it first using a function presented below.
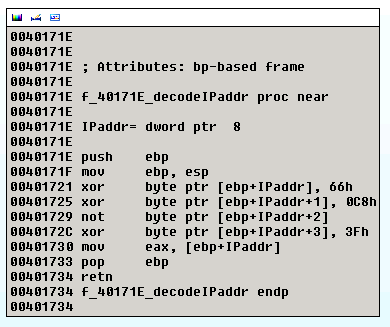
For example, if the DNS query returned IP address
, it will be decrypted to
.
How to recognize it in network traffic?
It is very easy to recognize the presence of this malware during a network traffic analysis. It uses a very specific HTTP header
. Additionaly, an answer from C&C server, always starts with the string
.

