-
List of malicious domains

With the help of telecommunications operators, we are starting a war against phishing sites that target personal data, banking information and social media accounts. In response to the growing number of phishing incidents related to the coronavirus pandemic, we are launching a list of malicious domains targeting Polish users. It …
Read more -
CFP Secure 2020

24th edition of iconic and the oldest cybersecurity conference in Poland. Do you love being on stage (or at least you don’t faint) and have something interesting to say? Apply! Why SECURE? There are many cybersecurity teams in Poland, but there is only one CERT Polska. And it guarantees …
Read more -
What’s up Emotet?
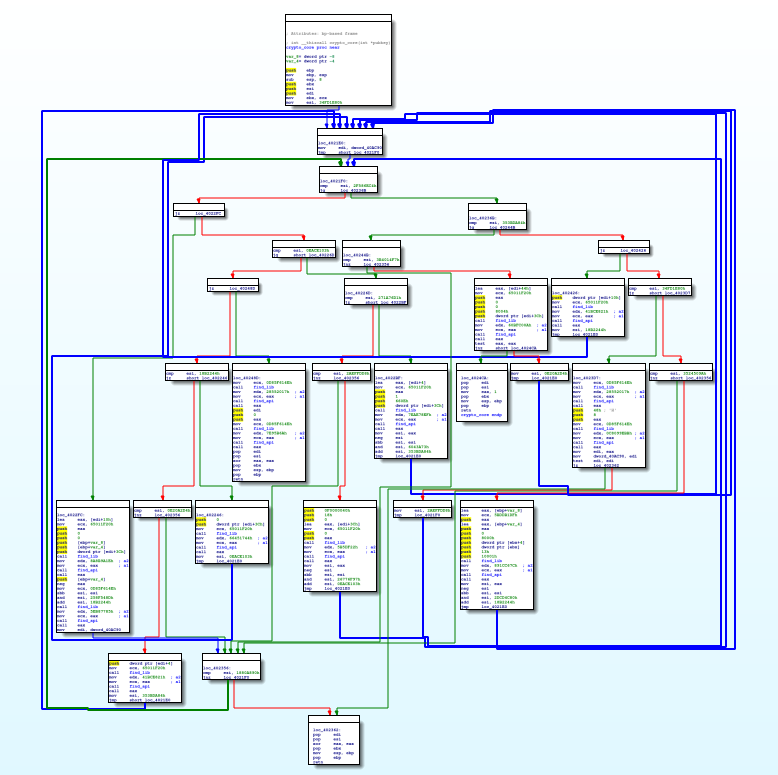
What’s up, Emotet? Emotet is one of the most widespread and havoc-wreaking malware families currently out there. Due to its modular structure, it’s able to easily evolve over time and gain new features without having to modify the core. Its first version dates back to 2014. Back then …
Read more -
Free decryption tool for Mapo ransomware
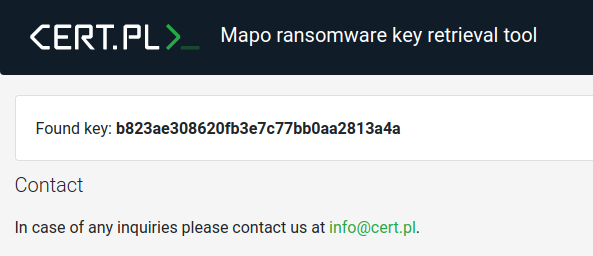
We are happy to announce that we are releasing a free decryption tool for the Mapo (a GarrantyDecrypt/Outsider variant) ransomware today. We would also like to thank Maciej Kotowicz of Kaspersky’s GReAT for sharing his insights on the ransomware’s encryption process. Our tool works with encrypted files …
Read more -
Brushaloader gaining new layers like a pro
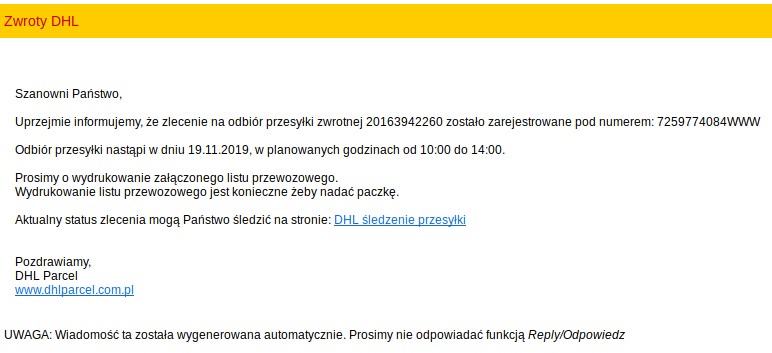
Yo dawg, I heard you like droppers so I put a dropper in your dropper On 2019-11-18 we received a report that some of Polish users have began receiving malspam imitating DHL: In this short article, we’ll take a look at the xls document that has been used as …
Read more -
SECURE 2019 – Call for Speakers

Call for Speakers for SECURE 2019 is now open. If you have an interesting topic and would like to share your ideas with a crowd of Polish and international IT security specialists, please consider submitting your proposal. You will find all applicable information below. SECURE 2019 will be held on …
Read more -
Incidents and incident reports in 2018

Publication of our annual report is coming soon. Editing is moving forward at full speed, but in the meantime we’d like to share some statistics concerning 2018. This statistics provide a big bicture of an IT security landscape in Poland and as well conclusions about major trends in this …
Read more -
Strengthening our malware analysis capabilities

During last year we have collaborated with Hatching.io on improving the open source Cuckoo Sandbox. The main works were focused on porting advanced mechanisms for memory analysis which were developed internally by our team in the previous years. The public release of the onemon marks the last stage of …
Read more -
Detricking TrickBot Loader
TrickBot (TrickLoader) is a modular financial malware that first surfaced in October in 20161. Almost immediately researchers have noticed similarities with a credential-stealer called Dyre. It is still believed that those two families might’ve been developed by the same actor. But in this article we will not focus …
Read more -
Recommendations on mitigation of man-in-the-middle phishing attacks (evilginx2/Modlishka)

CERT Polska has observed an interesting phishing technique used in attack against users of a popular Polish content aggregator. We have also noticed the emergence of a new tool called “Modlishka” whose purpose is to simplify and automate phishing attacks. In this article, we describe the way these highly-automated attacks …
Read more