-
13 October 2014 CERT Polska
ECSM HackMe challenge

October is a month designated by the European Commision and ENISA as a European Cyber Security Month. NASK and CERT Polska are one of the partners in this endeavor. Third week of October is dedicated to students and application security. For this reason we have prepared a HackMe challenge that …
Read more -
VBKlip 2.0: no clipboard, but Matrix-like effects

In the last few weeks we received information about a new kind of malware, similar to the VBKlip malware family. However, while reading these incident reports we got a bit of a science-fiction feeling. Users described that they went to the e-banking site and they tried to perform a wire …
Read more -
Android RAT malware spreading via torrents

In the last few days we observed a number of new attacks targeting the Polish Android users. Many Polish and foreign blogs reported the phishing e-mails using Kaspersky brand to convience user to install an apk file. Below some details of this attack, including the malware analysis, are provided. Thanks …
Read more -
AutoIt scripts are the new black for malware startups

AutoIt scripts use becomes more and more fashionable for malware obfuscators, cryptors and alike. Especially among the not-so-sophisticated malicious software. Recently we described the phishing attack targeted at Polish users using Booking.com and Allegro.pl. This attacked used AutoIt script (called RazorCrypt) in one of its stages in order …
Read more -
30 June 2014 CERT Polska
We see scanning for vulnerable BMC modules
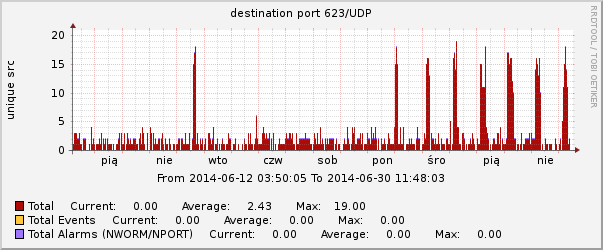
Since Dan Farmer published his latest article on BMC vulnerabilities, ARAKIS system records increased rate of UDP port 623 scans, coming from China, USA, Islandia, Romania and Netherlands. The revealed vulnerabilities allow to gain control of the servers’ online management modules, which control power and gathers status information from the …
Read more -
E-mail trojan attack on Booking.com and online auction website Allegro.pl clients

During the last few days, we have observed an attack on Polish users of auction website Allegro.pl and a hotel reservation portal – Booking.com. These attacks were directed at Polish users. Victims received a personalized e-mail that informed them that their account has been blocked either due to the …
Read more -
A look on the VBKlip “battlefield”

On multiple occasions we informed about a new threat to Polish online banking users, which we named VBKlip. This is a new kind of malware that substitutes the bank account number that has been copied to the clipboard. This works when we try to, e.g. pay a bill, and …
Read more -
Polish team wins NATO exercise

Locked Shields is an readiness testing exercise where security specialists teams from 17 countries compete defending a realistically simulated network from outside attacks. This year the winning team was from Poland, and it included representatives of CERT Polska. Other competitors were coming from Estonia, Finland, NATO CIRC, Italy, Spain, Germany …
Read more -
Annual cert.pl report

We have published our annual report, describing CERT Polska activities in 2013. The highlights of the document are: our botnets takeover summary, our malware analyses results, stopping rogue registrar Domain Silver Inc. and results of botnet sizes estimations done using new methodology. Full document in English can be downloaded HERE …
Read more -
Estimating size of the botnets in Poland

Annual CERT Polska report will soon be available on our website for download. This year we decided not only to include statistical data (which will be moved to a separate section), but also describe trends and events that were important according to us and were observed in the last year …
Read more